Do you want to avoid that your subscribers’ email clients mark your newsletters and automated emails as phishing emails? Do you want to make sure that no one sends emails in your company’s name?
Then set up SPF, DKIM, and DMARC as soon as possible. Or send your emails via trusted email marketing solutions.
Why do my subscribers mark my emails as phishing emails?
Do you know what happens after you send a newsletter or automated email from your email marketing service provider such as Automizy (or similar tools)?
Your subscribers’ ISPs (such as Gmail, Outlook, Yahoo, etc.) will check whether you are allowed to send them emails from the sender email.
For instance, you can’t send an email from you@google.com unless you own the google.com domain.
And if you don’t authenticate your emails, ISPs will mark your emails as a phishing email and block them.
It is nothing more than defending mailboxes from phishing and spam emails. Also, it helps you – as a legal sender domain – defend your own brand’s reputation: it prevents others to send emails in your name.
There are 3 ways to avoid this: set up SPF, DKIM a DMARC for your domain or use trusted email marketing providers.
How to authenticate your emails?
There are 3 ways to authenticate your emails and as a digital or an email marketer you have to know the basic concepts.
Therefore, the next 3 topics are about email authentication. It’s not that boring as you might think! 😉
If you are a small business, you just have to choose a good vendor (such as Automizy) because it solves this for you without any need of manual intervention from you.
But to help you understand how learn more!
Don’t care about Sender Policy Framework (SPF)
Basically, SPF authentication means that an email provider can send emails in your company’s name.
But there are lots of myths about SPF records on the web that don’t really tell you the truth. People don’t really understand the technology that provides this type of protection. Therefore, I explain how it truly works and what is the truth.
If you want to avoid email forgery (other people write emails in your name), lots of email marketing providers will suggest you set up an SPF record. They give you a command line that has a list of IP (SMTP server’s) addresses and you have to insert it to your domain’s DNS record.
Forget now, it doesn’t matter!
Lots of people think that the SPF authenticates the “envelope sender” or the “header sender” values of your emails. But in fact, it doesn’t.
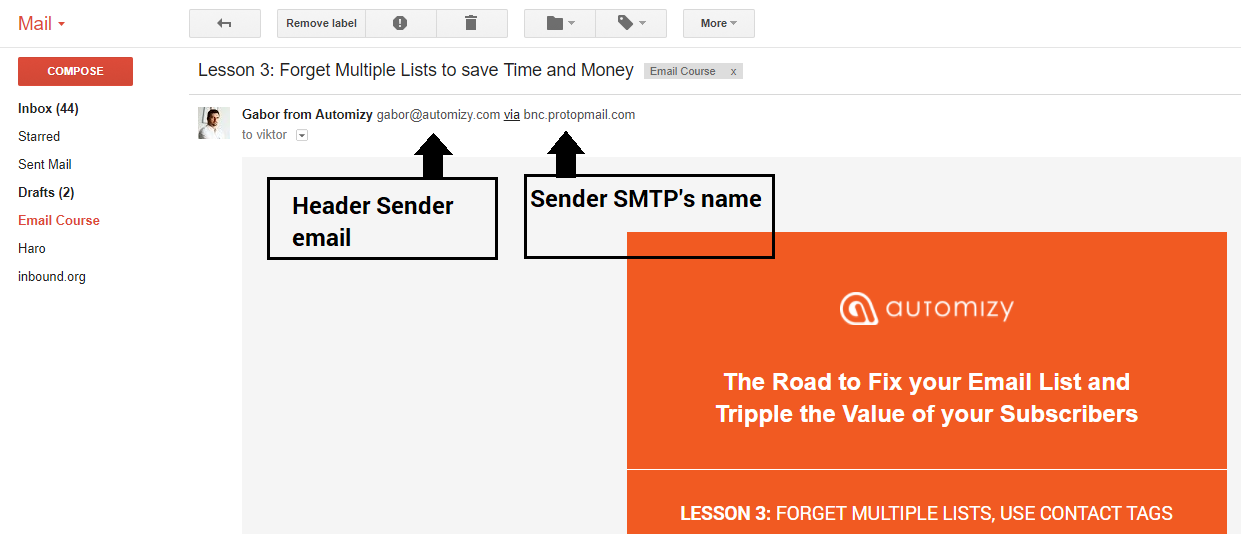
“Envelope sender” is the name of the SMTP server that truly sends your emails and it can’t be seen when your subscribers receive your emails. It’s just not visible to anyone. Lots of people think that this is the element that is authenticated by the SPF. Well, not at all, email providers can easily leave it out from your emails meta-descriptions.
“Header sender” is visible, it is the “from email” you usually can specify. It’s visible for your subscribers when they get your emails.
You can see it if you check a newsletter in your inbox (for example in Gmail) and you check the sender email there. You usually see a “via domain.com” extension after it (it is the name of the SMTP server that sent your email). But SPF doesn’t have anything to do with this value – anyone can customize their “from email” in an average email marketing tool.
So what does SPF truly authenticate and how to set it up?
It authenticates a lesser-known “MAIL FROM” value generated by your sender (SMTP) server that sends it to an ISP (Internet Service Provider such as Gmail, Yahoo, Outlook, etc.).
It tells the ISP that an email sending process got started with a specific “MAIL FROM” value. The SPF record tells that this sending process is valid. And that’s all, it doesn’t do more!
(To be honest, there are 2 more values that are used for authentication but those are exceptions and very rarely used.)
This value exists only in the sender SMTP servers and never cares whether you inserted SPF to your DNS record of your hosting server or not. You only have to do it if you want to set up “high-level” DKIM protection (but I will speak about it later on).
As almost every email marketing tool sends your emails from their own SMTPs, it’s more than enough if they tell the ISPs that they use their own MAIL FROM domains.
Therefore you don’t have to do anything with it. Unless you want to use your own customized MAIL FROM domain. (It is used mainly for enterprise businesses or well-known brands as it is needed to setup DMARC authentication which I will speak about later.)
So passing the SPF check should happen without doing anything. It authenticates the sender domain and tells ISPs (like Gmail, Yahoo or Outlook) that the email marketing tool can send emails in your name.
Make sure no one hijacks your emails with DomainKeys Identified Mail (DKIM)
DKIM makes sure that no one modifies the content of your email when it is going from the sender to the ISP.
So basically, it prevents others from adding malicious links and downloadable content to your existing emails.
It provides a sign to your emails that makes sure that nothing was modified in the email body. This authentication technology uses a combination of public key cryptography and DNS lookups to check the sender and the arrived emails’ differences.
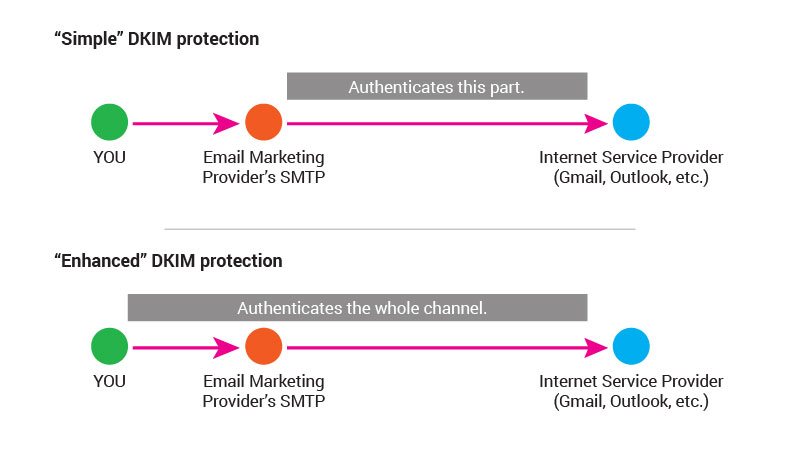
DKIM has 2 types:
- A simpler type
- An enhanced type
By default, better email marketing providers give you DKIM protection that makes sure that there won’t be any modification in the email body between the provider’s SMTP and the ISP. Usually, it’s more than enough for small businesses and you don’t have to do anything with it.
But if you want to make sure to completely authenticate your emails, you can set up your own domain for DKIM protection. In this case (and only in this specific case!) you have to insert the previously mentioned SPF record into your DNS server and also generate a Token there. (This process is unique to each service provider, at Automizy you just have to simply send us an email or in-app message and we’ll help you set it up.)
Use Domain-Based Message Authentication, Reporting & Conformance (DMARC) if you work for a well-known brand
In previous authentication methodologies, you could specify what are the legit email senders and email bodies. But DMARC specifies what should happen if the SPF or DKIM validation is not passed by an email.
DMARC is a policy that tells the email client what should happen if the SPF or DKIM sign is failed. Every business should set it up for them if they want this type of protection. It is a unique set of rules which can easily harm your own emails. Therefore, take care when you set it up for your company.
The reason why smaller brands don’t use this type of protection is that its main goal is to avoid phishing emails be sent in your brand’s name.
It means if your brand is well-known and has a good reputation the more cybercriminal will try to send emails in your company’s name to steal passwords and personal data from people. Usually, small businesses don’t have to use it at all.